SBOM (Software Bill of Materials)
A Software Bill of Materials (SBOM) is a comprehensive inventory of all software components, libraries, and dependencies used in an application. bifrost uses SBOMs to analyze your services for known vulnerabilities and security risks.
What SBOM upload enables in bifrost
Section titled “What SBOM upload enables in bifrost”Uploading an SBOM to bifrost enables:
- CVE Lookup: Automatically identify known vulnerabilities (CVEs) in your service dependencies and components
- CVE History Tracking: Track the evolution of vulnerabilities across different versions of your services over time
- CVE Analysis: Gain insights into which vulnerabilities are relevant to your specific service context, reducing noise from irrelevant CVEs
bifrost supports uploading multiple SBOMs per service version, allowing you to track vulnerabilities across different aspects of your application (e.g., separate SBOMs for different container images or dependency sets). Enabling a complete overview of your service’s security posture.
Supported SBOM formats
Section titled “Supported SBOM formats”bifrost supports the following SBOM formats:
- CycloneDX (JSON format)
- SPDX (JSON format)
Generating SBOMs
Section titled “Generating SBOMs”SBOMs can be generated using various tools depending on your stack:
Using GitHub’s built-in SBOM service
Section titled “Using GitHub’s built-in SBOM service”GitHub can automatically generate SBOMs for your repositories through the dependency graph feature. This is available for both public and private repositories and supports multiple ecosystems.
To export an SBOM from GitHub:
- Navigate to your repository on GitHub
- Go to the “Insights” tab
- Click on “Dependency graph” in the sidebar
- Click “Export SBOM” to download in SPDX format
For more details, see GitHub’s guide on exporting SBOMs.
For container images
Section titled “For container images”# Using Trivytrivy image --format cyclonedx <image> > sbom.jsonFor application dependencies
Section titled “For application dependencies”For applications, it’s recommended to generate SBOMs as part of your build process. Most modern programming languages and build tools have plugins or libraries available to generate SBOMs in CycloneDX or SPDX format. This ensures your SBOM accurately reflects your application’s dependencies at build time, which is important for accurate vulnerability tracking and compliance.
SBOM generation tools
Section titled “SBOM generation tools”- CycloneDX GoMod Generate SBOM - GitHub action to generate a CycloneDX SBOM for Go modules (uses
cyclonedx-gomod) - CycloneDX .NET Generate SBOM - GitHub action to generate a CycloneDX SBOM for .NET (uses
dotnet tool CycloneDX) - CycloneDX Node.js Generate SBOM - Generate a CycloneDX SBOM for Node.js (deprecated, use
npx @cyclonedx/cyclonedx-npminstead) - CycloneDX Python Generate SBOM - Generate a CycloneDX SBOM for Python
- CycloneDX Gradle Plugin - Gradle plugin to generate CycloneDX SBOMs for Java projects
- Syft – A CLI tool and Go library for generating SBOMs from container images and filesystems
- Microsoft SBOM Tool - Command-line tool to generate SBOMs in SPDX for a variety of languages and package managers
Uploading SBOMs
Section titled “Uploading SBOMs”SBOMs are uploaded to bifrost using the integration API. This associates the SBOM with a specific service version for vulnerability analysis. The SBOM can be uploaded during the build step before deployment (e.g., in CI/CD pipeline) or after the service has already been deployed.
Multiple SBOMs can be uploaded for the same service version, allowing you to track vulnerabilities across different components or images within a single version.
For full API details, see the OpenAPI specification.
API endpoint
Section titled “API endpoint”POST /api/v2/service/{service}/version/{serviceVersionName}/sbomParameters
Section titled “Parameters”service(path): Service name or IDserviceVersionName(path): Version name or aliasimage(query, optional): Container image reference (e.g.,registry/repo:tag)
Request body
Section titled “Request body”The SBOM document in JSON format (CycloneDX or SPDX).
Example
Section titled “Example”# Generate SBOM for a container imagetrivy image --format cyclonedx myapp:1.0.0 > sbom.json
# Upload SBOM to bifrostcurl -X POST \ "https://portal.bifrostsec.com/api/v2/service/myapp/version/1.0.0/sbom?image=myapp:1.0.0" \ -H "Authorization: Bearer $INTEGRATION_TOKEN" \ -H "Content-Type: application/json" \ --data-binary @sbom.jsonIntegration with CI/CD
Section titled “Integration with CI/CD”SBOMs are typically generated and uploaded as part of your CI/CD pipeline. Below is an example GitHub Actions workflow that builds code, generates an SBOM using the anchore/sbom-action, and uploads it to bifrost using the bifrostsec/submit-sbom-action. You can read more about the GitHub Action here.
name: buildon: pull_request:
jobs: build: name: Build and submit SBOM runs-on: ubuntu-latest steps: - name: Checkout Code uses: actions/checkout@v6
- name: Build code run: make build
# Generate SBOM using anchore/sbom-action (Syft) - name: Generate SBOM uses: anchore/sbom-action@v0.21.1 with: path: . format: spdx-json output-file: sbom.spdx.json
# Send SBOM to bifrost - name: Send SBOM to bifrost uses: bifrostsec/submit-sbom-action@v1 with: api-token: ${{ secrets.BIFROST_API_TOKEN }} service: 'my-service' service-version: 'v1.0.0' sbom-path: 'sbom.spdx.json'Vulnerability analysis
Section titled “Vulnerability analysis”After uploading an SBOM, bifrost automatically:
- Analyzes all components and dependencies in the SBOM
- Matches them against known vulnerability databases
- Identifies relevant CVEs for your specific service context
- Provides actionable recommendations for remediation
- Analyzes your security profiles to filter out irrelevant CVEs (requires your organization AI-settings to be enabled)
You can view vulnerability results in the bifrost portal under your service version details.
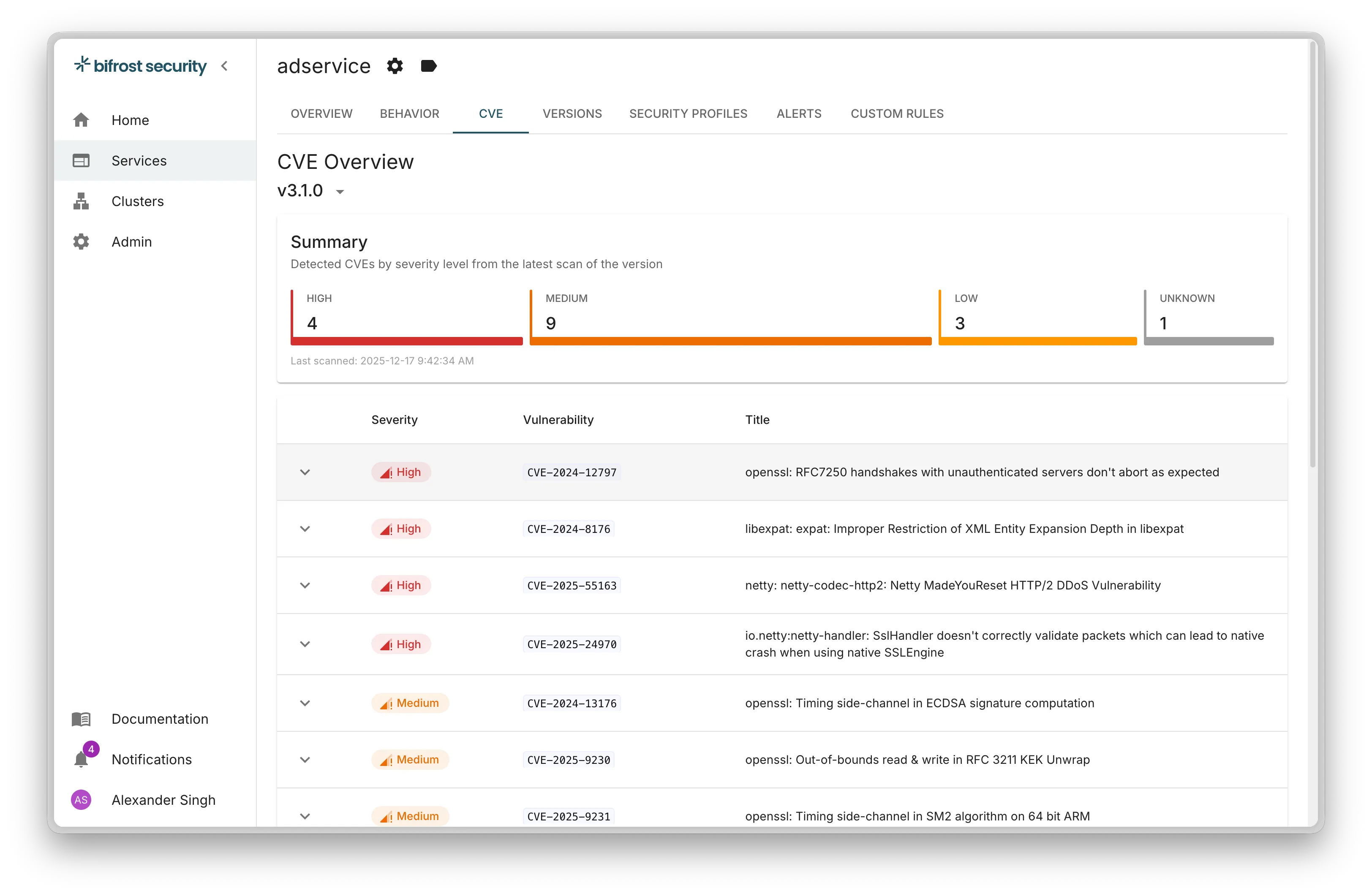
Best practices
Section titled “Best practices”- Generate SBOMs for every build: Include SBOM generation in your CI/CD pipeline
- Use the image parameter: When uploading SBOMs for container images, always include the image reference for better tracking
- Keep SBOMs up to date: Upload a new SBOM whenever dependencies change
- Include all layers: For container images, ensure your SBOM tool scans all layers, not just the application code